Revinetd is a GNU implementation of the TCP gender changer. It operates in two modes, listen-listen and connect-connect. It can be used to forward traffic through firewalls where outbound rule sets are more liberal than inbound rules.
Disclaimer : This tool should only be used with the consent of the machine's owners. Connecting to machines without authorization is illegal.
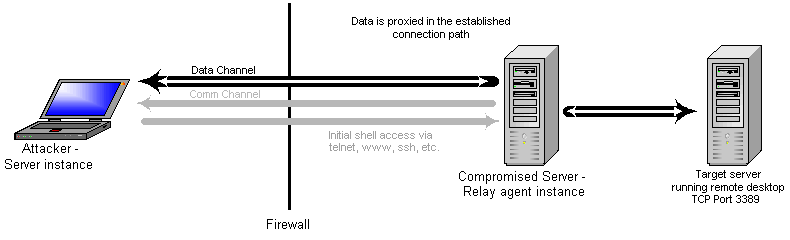
First, the attacking machine must establish shell access in some manner. This can be done a variety of ways. But there must be a way to upload revinetd and start it up. In this case we are interested in connecting to a remote desktop connection running on port 3389. The firewall allows only one port inbound to the compromised server, and we are using it for shell access. For outbound connectivity, the firewall allows connections on several ports.
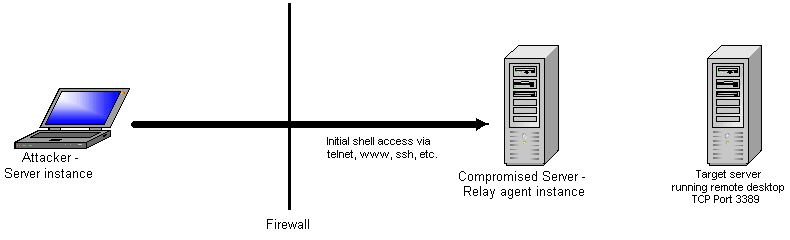
Now the pen tester can initialize the revinetd server instance on his laptop and a relay agent instance on the compromised server.
For server:
For relay agent:
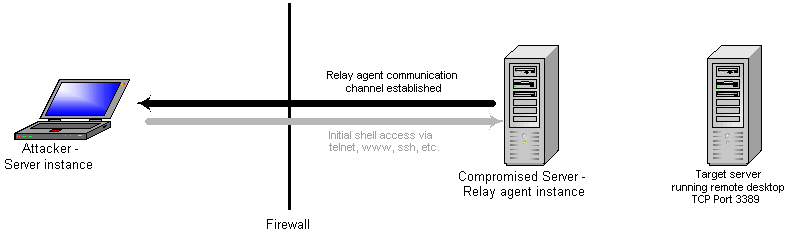
Now the client software connects to the server instance. Upon sensing the connection, the server sends a request on the communications channel so the relay agent can request a new data connection. Since the compromised server is the initiator of the data channel, we will most likely have more ports to choose from since outbound firewall rule sets tend to be more liberal.
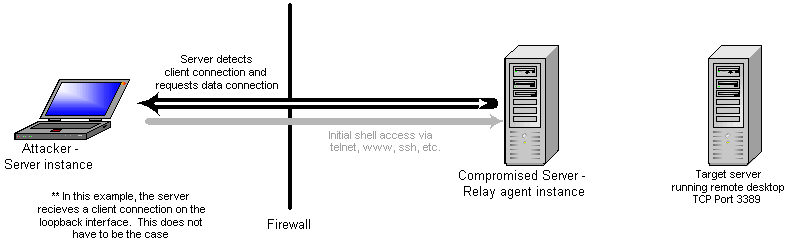
The relay agent receives the message from the server and establishes a new connection to the server instance. It also connects to the target server to create a proxy port pair for data relay. When the server receives the data channel connection, it creates a proxy port pair with the client connection.
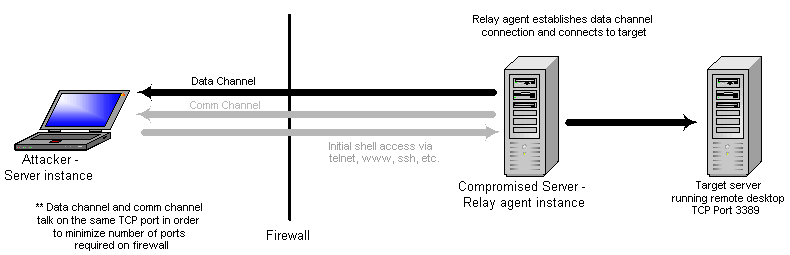
The proxy port pairs now relay data until communications are finished. Concurrent connections can occur as long as the communications channel is established.
Back to main page.